In the digital world, protecting your creative work is of great importance, and that’s where cybersecurity comes in.
Cybersecurity acts as your defense system against various threats that aim to mess with your sensitive information and creative works. It involves a set of careful practices, technologies, and strategies to keep your data, networks, and computer systems from unauthorized access and potential harm.
This article explores how cybersecurity can protect your intellectual property.
We’ll cover measures like access controls, encryption, monitoring tools, and collaborations between creators and cybersecurity experts. We’ll also provide you with insights into strategies for preventing copyright issues and a complete view of how important cybersecurity is for preventing copyright infringement in the digital world.
- Cybersecurity prevents copyright infringement by enforcing access controls, ensuring only authorized users have access to copyrighted materials.
- Various tools such as digital watermarking, intrusion detection systems, and encryption collectively contribute to a multi-layered approach to protecting copyrighted materials.
- Intellectual property is not only valuable to creators and individual companies but also holds national significance.
Table of Contents
How Can Cybersecurity Help Prevent Copyright Infringement?
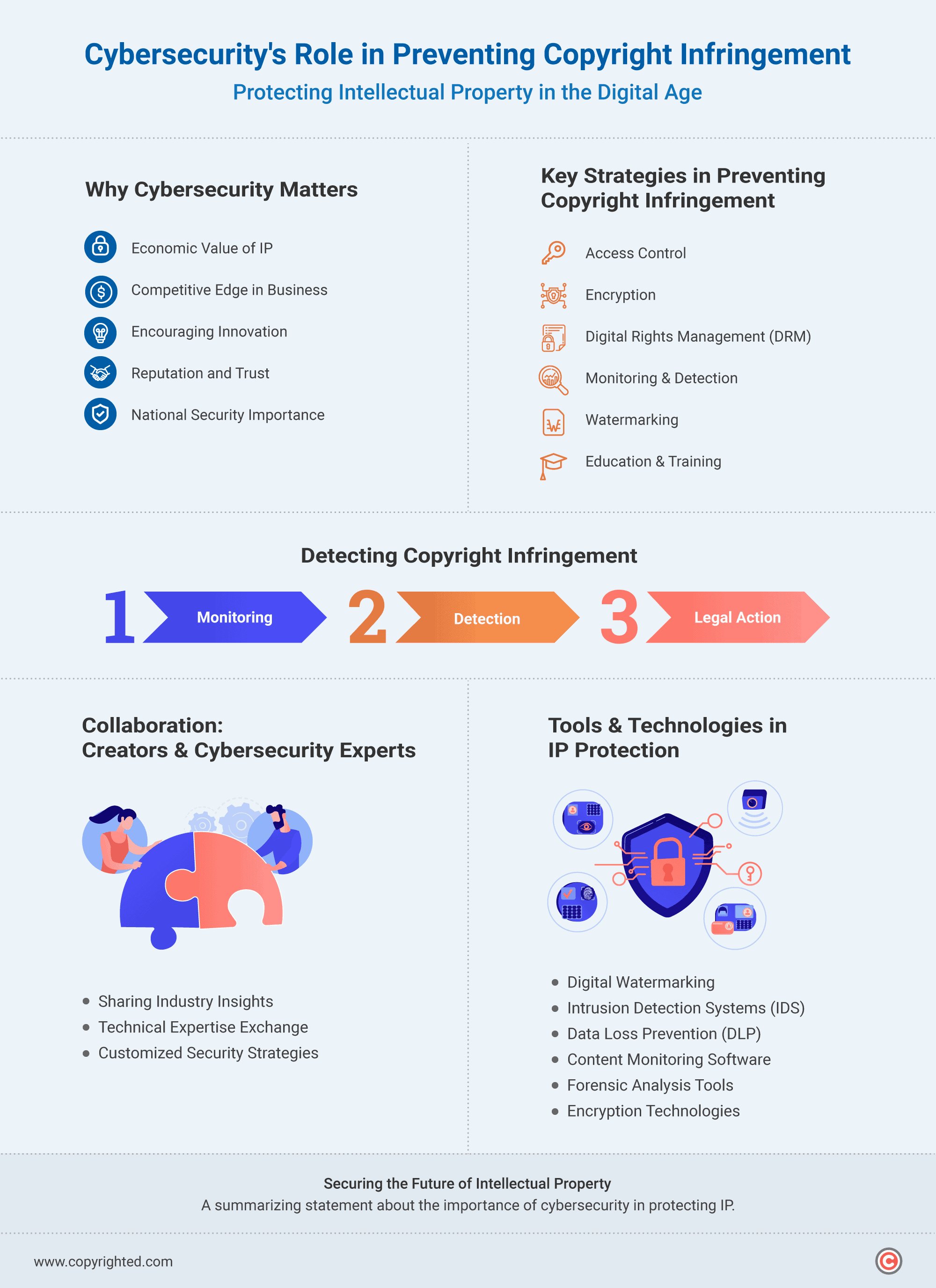
Cybersecurity plays an important role in preventing copyright infringement through the implementation of various measures.
One key aspect is the enforcement of access controls. This means ensuring that only authorized users have access to copyrighted materials.
Authentication mechanisms, user permissions, and continuous monitoring of access logs are employed to identify and address any unauthorized attempts.
Encryption is another significant component of cybersecurity in this context.
By utilizing encryption techniques, digital content can be protected during transmission and storage. This safeguards against unauthorized parties intercepting or tampering with copyrighted material, especially when sharing sensitive content over networks or storing it in cloud-based platforms.
Digital Rights Management (DRM) technologies provide a systematic approach to controlling and managing the usage of digital content.
DRM solutions often include encryption, access controls, and licensing mechanisms that define how users can interact with copyrighted materials. This helps prevent unauthorized copying, modification, and illegal duplication of copyrighted works.
Monitoring and detection through cybersecurity tools are key to identifying any suspicious or unauthorized access to copyrighted content. Intrusion detection systems, data loss prevention tools, and advanced analytics contribute to the identification of potential copyright infringement incidents.
In some cases, unauthorized users accessing or distributing content may face copyright infringement threats if rights holders pursue legal remedies.
Watermarking, involving the embedding of imperceptible information into digital files, is an additional measure in copyright infringement cybersecurity. This also helps in tracing the source of copyright violations.
Moreover, education and training programs are essential in enhancing cybersecurity measures. Raising awareness among users about copyright laws and infringement risks can contribute to more effective implementation of cybersecurity strategies.
How is Copyright Infringement Detected Using Cybersecurity?
Copyright infringement is detected using cybersecurity through a combination of monitoring tools, digital forensics, and collaboration between content creators and cybersecurity experts. You get caught for copyright infringement through the analysis of network activities, suspicious behavior patterns, and the use of technologies like watermarking to trace the origin of unauthorized distribution.
In addition to proactive cybersecurity measures, copyright infringement raids are also important in combating the unauthorized distribution of copyrighted materials.
Law enforcement agencies, often in collaboration with cybersecurity experts, conduct raids based on information gathered through digital investigations. These raids involve seizing physical and digital evidence, such as counterfeit goods, servers hosting infringing content, or devices used in the commission of copyright infringement.
Many people also ask, is it illegal to watch copyrighted material online without permission? The answer largely depends on jurisdiction, but in general, knowingly accessing pirated or unauthorized content can expose users to legal risks and penalties.
The collaboration between cybersecurity experts and law enforcement agencies enhances the effectiveness of these raids, making them an integral part of the broader strategy to protect intellectual property in the digital landscape.
Collaborative Efforts Between Creators and Cybersecurity Experts
As a content creator, you are the primary stakeholder in protecting your work since you know it best. Cybersecurity experts, on the other hand, contribute technical skills and keep up with emerging threats.
Creators provide insights into their content, demographics, and distribution channels, helping cybersecurity experts customize strategies. This collaboration allows for a targeted approach, considering the unique challenges faced by each creator.
Creators also share industry insights, helping cybersecurity experts stay ahead of piracy trends and emerging threats. Through open communication, creators can contribute to improving cybersecurity measures.
Cybersecurity experts, with technical expertise, develop and implement measures to detect and prevent copyright infringement. This includes deploying tools, monitoring systems, and encryption technologies for a robust defense against unauthorized use.
Beyond technology, cybersecurity experts also teach creators best practices for securing content and staying vigilant against threats.
This collaboration is mutually beneficial – creators gain technical expertise and access to advanced strategies, while cybersecurity experts acquire industry-specific knowledge to address creative challenges.
Tools and Technologies in Protecting Intellectual Property
In cybersecurity, various tools and technologies are employed to protect intellectual property and detect instances of copyright infringement. These tools are critical in protecting digital content and identifying unauthorized use.
- Digital Watermarking: Digital watermarking is a technique involving the embedding of imperceptible information within digital files, creating a unique identifier. This identifier helps in tracing the origin of copyrighted material, facilitating the detection of unauthorized distribution. It acts as a digital fingerprint for content.
- Intrusion Detection Systems (IDS): IDS monitors network or system activities, identifying suspicious behavior or patterns that may suggest unauthorized access or use of copyrighted content. Early detection through IDS allows for timely intervention, preventing potential copyright infringements before they escalate.
- Data Loss Prevention (DLP) Tools: DLP tools focus on preventing unauthorized access, use, or distribution of sensitive data, including copyrighted material. These tools monitor and control data transfers, ensuring compliance with copyright policies and preventing unintended or malicious dissemination of content.
- Content Monitoring and Analysis Software: Specialized software is designed for monitoring and analyzing online content including websites, social media platforms, and file-sharing networks to identify instances of copyright infringement. This technology aids in proactively detecting and addressing unauthorized use of intellectual property across various online platforms.
- Forensic Analysis Tools: Digital forensics tools are instrumental in investigating copyright infringement incidents. They analyze digital evidence, such as files or network logs, reconstruct events, and gather information for potential legal actions.
- Encryption Technologies: Encryption serves as a strong protection against data breaches and unauthorized access to sensitive content. It ensures that only authorized users can access and use copyrighted materials, preventing unauthorized interception or tampering.
These tools collectively establish a multi-layered approach to the detection and prevention of copyright infringement. By using a combination of these tools, content creators and cybersecurity experts can collaborate effectively to secure intellectual property.
Why is Cybersecurity Important to Intellectual Property?
Cybersecurity is important to intellectual property because it safeguards sensitive information, technologies, and innovations from unauthorized access, theft, or compromise.
In terms of economic impact, intellectual property often serves as the cornerstone of a company’s economic value. Unauthorized access or theft of proprietary information, including patents, trade secrets, or innovative technologies, can lead to significant financial losses.
Therefore, protecting intellectual property is not only about preserving creativity but also maintaining the economic viability of businesses.
Moreover, intellectual property provides a competitive edge in the business landscape.
Companies invest in research and development to create unique products or services, and the protection of these innovations through patents or copyrights allows them to differentiate themselves in the market. Preserving this competitive advantage needs cybersecurity measures to prevent unauthorized access or replication of valuable intellectual assets.
The promise of protection for intellectual property also plays a key role in encouraging innovation. Companies are more likely to invest in research and development when they have confidence that their intellectual assets will be protected.
In this context, cybersecurity assumes an important role in ensuring that these innovations remain confidential and protected from theft or industrial espionage, creating a culture of continuous innovation.
A security breach that compromises intellectual property can also result in severe reputational damage.
Trust is a critical component of any business relationship, and customers, partners, and investors may lose confidence in an organization that fails to protect its intellectual assets. Cybersecurity measures are thus essential for maintaining trust and protecting the reputation of individuals and companies alike.
Beyond individual businesses, intellectual property holds national importance, representing critical technologies or innovations that have significance for a country. Protecting intellectual property from cyber threats becomes a matter of national security.
In summary, implementing effective cybersecurity measures becomes paramount to protect intellectual property from the evolving landscape of cyber threats, ensuring the continued growth and prosperity of individuals, businesses, and nations.
Frequently Asked Questions
Can a copyright infringement result from a cybercrime?
Yes, copyright infringement can result from cybercrimes when unauthorized copying, distribution, or use of copyrighted material occurs through digital means, such as online piracy or illegal file-sharing.
What are the different copyright infringement actions?
Copyright infringement actions include unauthorized reproduction, distribution, display, or performance of copyrighted works. This can happen through copying, sharing, selling, or using original work without permission of the copyright holder.
What is copyright in cyberethics?
In cyberethics, copyright refers to the ethical considerations and principles surrounding the protection of intellectual property in the digital space. It involves respecting creators’ rights, avoiding plagiarism, and adhering to legal and ethical standards related to digital content.
How do hackers steal intellectual property?
Hackers can steal intellectual property through various means, including unauthorized access to databases, exploiting vulnerabilities in computer systems, using malware, or conducting phishing attacks to gain access to confidential information, trade secrets, or copyrighted material.
Is copyright infringement a cybercrime?
Yes, copyright infringement can be considered a cybercrime when it involves the unauthorized use, reproduction, or distribution of copyrighted material through digital channels, violating intellectual property rights in the online domain.


