Welcome to the digital age. A time when businesses thrive on the power of their digital assets. From valuable customer data to proprietary software and intellectual property, these assets are the lifeblood of modern organizations.
But, in the words of our favorite hero… “With great digital power comes great responsibility.” As technology advances, so do the threats that lurk in the digital realm. That’s why it’s vital you learn how to take the right steps to protect digital assets.
In this article, we’ll explore how to protect digital assets. We’ll review the three types of digital assets that businesses need to protect and also touch base on the various cyber threats that you should keep an eye on.
Finally, we’ll also provide you with practical strategies to secure and protect your digital assets and equip you with the knowledge and tools to fortify your defenses. Let’s get started.
Table of Contents
3 Types of Digital Business Assets
There are three types of assets that usually hold the most value and potential for online businesses.
Intellectual property
Imagine a world without inventions, innovations, or captivating works of art. Sounds dull, right? Well, intellectual property (IP) is the magical fuel that drives creativity and progress in our digital age. It includes patents, trademarks, copyrights, and trade secrets that businesses create and cherish.
Think of IP as the cape that protects your unique ideas from falling into the wrong hands. It covers everything from groundbreaking technologies to catchy slogans and artistic masterpieces.
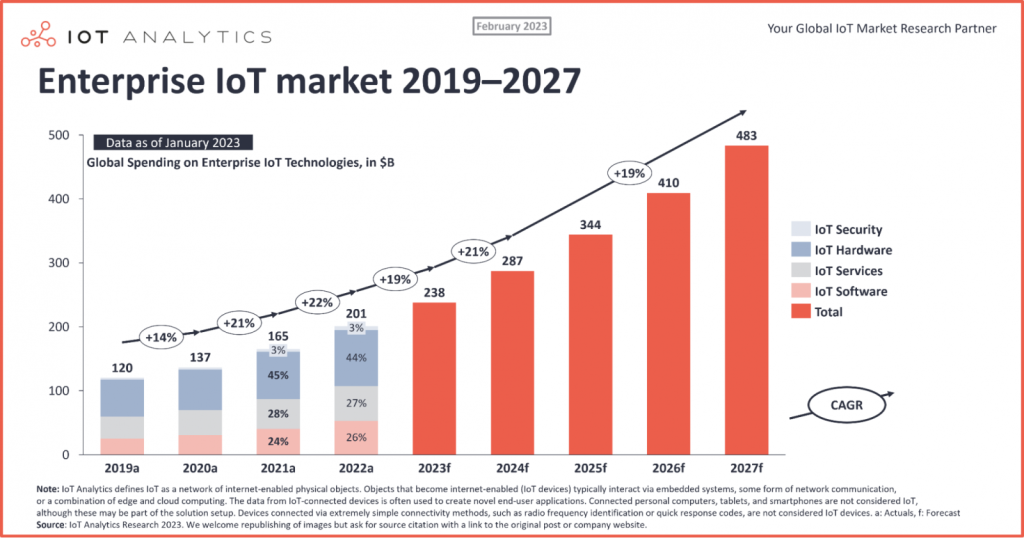
One industry really shaping the future of intellectual property is IOT. With a projected market value of $483 billion by 2027, the IoT industry is buzzing with innovation and growth. Companies are filing patents at an unprecedented rate, recognizing the immense potential and competitive advantage that IoT brings.
Protecting your intellectual property ensures that your hard work, creativity, and ingenuity remain yours. It grants you the power to control how your ideas are used, reap the benefits of your innovations, and build a competitive edge in the marketplace.
Trade secrets
Ah, the allure of trade secrets! These gems of knowledge hold the power to propel your business to new heights. They’re the secret recipes, manufacturing processes, or marketing strategies that make your company stand out from the competition.
Think of Coca-Cola’s top-secret formula or Google’s search algorithm—these trade secrets are the keys to their success.
Trade secrets are carefully guarded within the confines of your organization. They are the result of years of experimentation, innovation, and meticulous refinement.
When protected effectively, they give you a competitive edge, allowing you to maintain your market position and thrive in an ever-evolving business landscape.
These secrets are not something you share with just anyone. They are your special ingredients, your secret sauce. Just like superheroes with alter egos, you keep your trade secrets hidden from prying eyes.
You rely on nondisclosure agreements, tight security measures, and strict internal controls to ensure their confidentiality.
Customer data
Data is worth its weight in gold these days. It holds invaluable insights into your customers’ preferences, behaviors, and needs. By harnessing this data, you can create personalized experiences that leave your customers in awe.
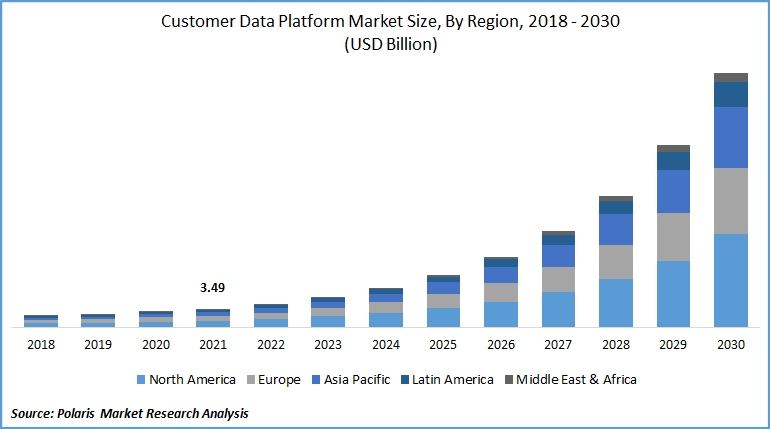
According to Polaris Market Research, the customer data platform market is expected to grow to around 4.98 billion USD by 2030. Customer data leads you to the riches of customer loyalty and satisfaction. It includes information such as purchase history, demographic data, and online interactions.
Protecting customer data is not only an ethical imperative but also crucial for maintaining trust and complying with privacy regulations.
Intellectual property, trade secrets, and customer data are the heart and soul of digital business. By understanding their significance and taking proactive measures to safeguard them, you become the fearless hero of your digital realm.
Cyber threats to keep an eye on
You should be aware of the villains lurking in the shadows. Here are the most common three most notorious adversaries that every business must be aware of:
Phishing attacks
Picture this – a crafty cybercriminal posing as a friendly acquaintance, attempting to trick you into revealing sensitive information. That’s the essence of a phishing attack. These mischievous scammers use cunning tactics, like cleverly crafted emails or enticing links, to steal your personal or login details.
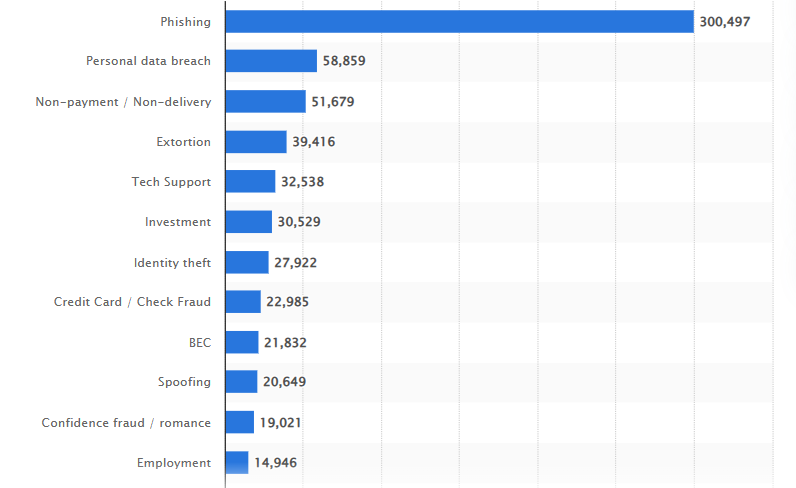
Phishing attacks are like chameleons, constantly changing their appearance to blend in with the digital landscape. They can target anyone, from the lowliest intern to the mightiest CEO.
And believe it or not, they are actually the most commonly reported type of cybercrime, with over 300,000 incidents reported in the US just last year!
By staying vigilant and mastering the art of spotting suspicious emails, you can thwart these deceitful attempts and protect your digital kingdom.
Malware and ransomware
Enter the world of malware and ransomware, where villains lurk in the darkest corners of the internet. These digital baddies come disguised as innocent files, applications, or even friendly-looking websites.
Once they infiltrate your system, they wreak havoc — stealing your data, causing system crashes, or worse, holding your files hostage.
Insider threats
Beware, for not all villains wear masks. Some may walk among us disguised as trusted allies — the dreaded insider threats. These cunning adversaries have access to your sensitive information. They can exploit their privileges for personal gain or, in some cases, unwittingly become conduits for cyberattacks.
Insider threats are like a plot twist in a thrilling story. They can be disgruntled employees seeking revenge through stolen content, unsuspecting individuals falling victim to social engineering, or even well-meaning team members inadvertently leaking confidential data.
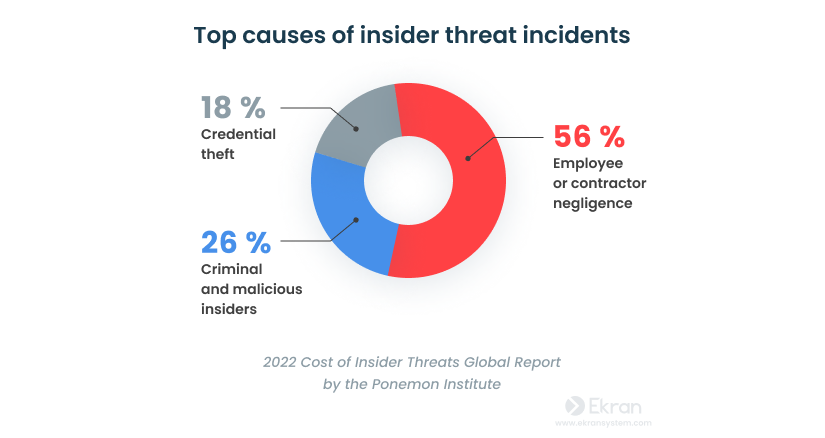
The main cause of this incident, however, is employee or contractor negligence, with 56% of these incidents being down to this. By implementing robust access controls, regular training programs, and fostering a culture of cybersecurity awareness, you can defend your digital kingdom from these unexpected foes.
So, as you navigate the treacherous digital landscape, be ever watchful of phishing attacks, malware and ransomware, and insider threats. With your wits sharpened and your defenses fortified, you’ll be ready to take on these dastardly foes and emerge victorious.
How to Secure and Protect Your Digital Assets
There are, of course, a few things you can do to minimize the risks and threats. As long as you follow these steps, the likelihood of dealing with an unexpected thread will be much lower.
Use Strong Passwords
You’re going to want to set up strong access controls like sturdy locks by using robust passwords and assigning user permissions wisely.

Let’s see this in action, shall we? Suppose you have a team of talented developers working on various projects. You implement a password policy that encourages them to create robust passwords, such as combining uppercase and lowercase letters, numbers, and special characters.
For example, instead of a weak password like “1234567890,” they might choose a strong password like “T3ch@#2023!” This ensures that cracking the lock becomes nearly impossible for potential intruders.
Always Authenticate
Now that you’ve set up strong passwords as your first line of defense, it’s time to reinforce your stronghold with an additional layer of protection — authentication.
Authentication is like a secret handshake, verifying the identity of those who seek access to your digital kingdom. It ensures that only authorized individuals can unlock the doors to your digital assets.
One popular authentication method is two-factor authentication (2FA). Think of it as an extra set of keys, adding an additional hurdle for would-be intruders.
With 2FA, after entering their password, users must provide a second form of verification, such as a unique code sent to their mobile device or a biometric scan like a fingerprint or face recognition.
By implementing two-factor authentication, you create an impenetrable fortress around your digital assets. Even if a malicious actor somehow gets hold of a password, they’ll be halted by the second layer of authentication. It’s like trying to pick a lock while simultaneously solving a complex riddle—nearly impossible!
Now, imagine this scenario: a would-be intruder manages to obtain an employee’s login credentials. However, thanks to two-factor authentication, they hit a dead-end when they’re unable to provide the second authentication factor.
Your assets remain safe and sound, protected by the power of authentication.
Encrypt Sensitive Data
Your sensitive data are like classified documents. Encrypting them is like sealing them inside an impenetrable vault. It’s as if you’re transforming your secrets into an ancient language that only trusted allies can decipher. So, wrap your data in a cloak of encryption and keep it safe from prying eyes.
You can also use role-based encryption to further protect digital assets. It allows authorized individuals with specific roles to decrypt and access encrypted data.
With role-based encryption, only employees assigned with the right roles can unlock and view the decrypted information, ensuring that sensitive data remains confidential.
To further enhance the security of your digital assets, it’s essential to implement effective password management for teams. Passwords act as the keys to your digital kingdom, and ensuring their strength and confidentiality is crucial.
By using password management tools or solutions, you can enforce strong password policies, encourage employees to create robust passwords, and securely store and manage their credentials.
This helps minimize the risk of unauthorized access and strengthens the overall security posture of your organization.
Additionally, password management solutions often offer features like multi-factor authentication and password-sharing capabilities, enabling teams to collaborate securely while maintaining control and protection over their digital assets.
You should also review how you process and store data. Data frameworks like RDD can help protect your data while still allowing access. By implementing a robust data management process, you can protect your data from unauthorized access both within and outside of your organization.
Patch and Update Software Regularly
Keeping your software up to date is a vital part of protecting your valuable digital assets. Software updates often include important bug fixes and security patches that address known vulnerabilities.
By promptly installing these updates, you close potential entry points that cybercriminals could exploit to gain unauthorized access to your systems.
Plus, hackers are constantly developing new techniques to breach security measures. Regular software updates ensure that you have the latest defenses in place, equipped with the necessary tools to counter emerging threats and stay one step ahead of potential attacks.
To make patching and updating easier, consider enabling automatic updates. Many software applications offer automatic update options. Enabling this feature ensures that critical updates are installed without requiring manual intervention, keeping your systems protected without added hassle.
Final Words
Your intellectual property, trade secrets, and customer data are the lifeblood of your organization, and protecting them is paramount.
Phishing attacks, malware and ransomware, and insider threats aren’t going anywhere. However, with knowledge and the right strategies, we can outsmart these foes and protect what is rightfully ours.
By using strong passwords, always authenticating, encrypting sensitive data, patching and updating software regularly, and enabling two-factor authentication, you fortify your digital fortress against potential breaches.
This journey is not a one-time event but an ongoing commitment. Cybersecurity is a continuous effort that requires vigilance, adaptability, and a willingness to stay informed about emerging threats.


